Abstract:
Caller ID solutions have been integral to modern telephony, enabling recipients to see who is calling before they answer. However, the scope of caller identification has grown more complex over time, moving from simple Caller Name (CNAM) lookups to advanced Branded Caller ID (BCID) frameworks. This article explores the evolution of caller ID services, contrasting how CNAM and BCID differ in technology, business models, and user uptake. We also examine the latest industry efforts—spearheaded by the CTIA—to deploy a unified BCID service that leverages STIR/SHAKEN protocols. By highlighting how providers like TNS, First Orion, Hiya, and major U.S. carriers are embracing or transitioning to this new BCID standard, the article discusses how these developments aim to restore trust in voice communications.
1. Introduction
Caller identification technologies have long been central to consumer telephony. Initially, these systems provided simple numeric caller ID, which then evolved to include names and, more recently, brand-specific information. While CNAM (Caller Name) services remain a backbone of caller ID, Branded Caller ID (BCID) offers businesses a way to display logos, detailed brand names, and verified call reasons.
Such technologies have become increasingly significant amid widespread robocalls and spoofing, which erode consumer trust in voice calls. The recent adoption of the STIR/SHAKEN framework, alongside new industry standards from the CTIA, signals a shift toward more sophisticated and verifiable caller ID ecosystems.
2. Overview of CNAM
2.1 Definition and Function
CNAM, or Caller Name, is a service that associates a phone number with a textual name displayed on the recipient’s phone. It traditionally shows up to 15 characters of alpha-numeric text, sourced from either a local database or national CNAM database providers.
2.2 How CNAM is Paid For
- Consumer-Funded: In many traditional landline and wireless services, the end user (subscriber) pays for caller ID as part of a calling plan or as an add-on feature.
- Database Queries: When a call is placed, a lookup is performed against a CNAM database, incurring a small query fee typically shouldered by the terminating carrier.
2.3 Challenges with CNAM Adoption and Trust
- Limited Adoption: A significant portion of subscribers do not have CNAM service enabled. By some industry estimates, fewer than half of mobile users in the U.S. actively pay for or enable caller name display features.
- No Formal Vetting: CNAM databases do not typically require a stringent verification or vetting process. As a result, it is possible for callers to provision inaccurate or misleading caller names.
- Lower Trust Level: Because CNAM lacks cryptographic verification and is prone to outdated or inaccurate data, consumer confidence in basic caller ID has declined, especially with the rise of spoofing.
3. Emergence of Branded Caller ID (BCID)
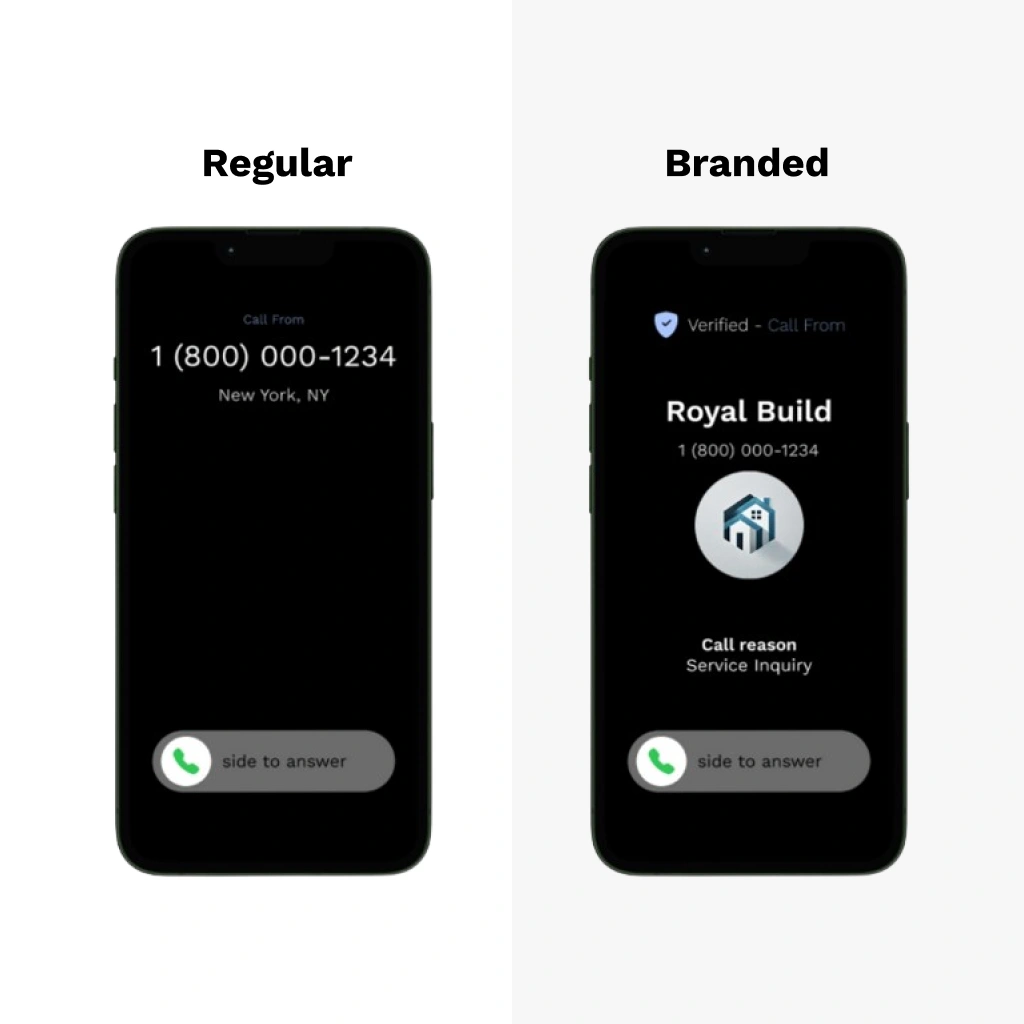
3.1 What Is Branded Caller ID?
Branded Caller ID (BCID) moves beyond simple CNAM text to a richer, verified identity display. This may include:
- Company Logo or Icon
- Extended Business Name (overcoming CNAM’s 15-character limit)
- Reason for Calling (e.g., “Bank Fraud Alert”)
- Verification Seal (indicating authenticity)
3.2 Business-Funded Model
Unlike CNAM, BCID is primarily paid for by businesses. By investing in BCID, organizations can reduce the likelihood of their calls being mistaken for spam and provide greater transparency to consumers. This contrasts with traditional CNAM, where end users generally foot the bill for seeing caller names.
3.3 Early Market Solutions: TNS, First Orion, Hiya
Prior to the new unified CTIA framework, multiple providers offered “enhanced” caller ID solutions:
- TNS: Provided cross-carrier ID and reputation scoring.
- First Orion: Focused on branded communication and call protection features.
- Hiya: Offered spam blocking, branded caller ID, and analytics, often pre-installed on smartphones.
These solutions required partnerships with individual carriers or OEMs (phone manufacturers) to display branded information. Implementation and user experiences varied based on which carrier or device a subscriber used.
4. Technological Underpinnings: STIR/SHAKEN and BCID
4.1 STIR/SHAKEN Basics
STIR/SHAKEN is a framework designed to authenticate and verify caller identity on IP-based networks:
- STIR (Secure Telephony Identity Revisited): A set of protocols for cryptographically signing calls.
- SHAKEN (Signature-based Handling of Asserted Information Using toKENs): Specifies how carriers implement STIR across their networks.
When a call is placed, the originating carrier attaches a cryptographic signature to the SIP header, indicating the call’s level of attestation. The terminating carrier checks this signature before delivering the call, helping to detect spoofed or fraudulent calls.
4.2 BCID Integration with STIR/SHAKEN
The new BCID services being launched under CTIA guidelines leverage the STIR/SHAKEN framework so that the displayed brand information is cryptographically verified. Essentially:
- Business Registration: The business registers its brand and call reason with an approved BCID provider.
- Origination: The call is signed with a STIR/SHAKEN token containing meta-information about the brand.
- Termination: The user’s carrier verifies the token. If valid, the device can display the brand logo, name, or other details—ensuring a “trusted” label rather than an easily spoofed text field.
5. The New Unified BCID Service from CTIA
5.1 Motivation and Rollout
The CTIA recognized that disjointed branded caller ID offerings confused consumers and limited business adoption. A unified approach simplifies the process for businesses, requiring them to register once and ensure consistent branding across carriers.
- T-Mobile: Already operational with the new BCID standard.
- Verizon: Planned to launch in Q1 of this year.
- AT&T: Expected to roll out by year-end.
5.2 Key Differences from Older Solutions
- Standardized Framework: Instead of siloed integrations (e.g., TNS, First Orion, Hiya each negotiating with carriers), the CTIA-led system provides an industry-wide standard.
- Better Consumer Reach: A unified approach means calls display branded info regardless of the subscriber’s carrier, provided they have a compatible device.
- Mandatory Verification: Under STIR/SHAKEN, calls must be cryptographically signed for BCID to be displayed, reducing spam calls that fake brand names.
5.3 Operational Mechanics
- Business Registration: A company enrolls with a BCID provider recognized by CTIA and supplies branding material plus call use cases.
- Verification & Token Generation: The provider issues cryptographic certificates matching phone numbers.
- Call Origination: Calls are placed through the business’s telecom channel, embedding the BCID info in the SIP header alongside a STIR/SHAKEN signature.
- Call Termination: The carrier checks the signature, verifying the call’s authenticity, and displays brand info if valid.
6. Restoring Trust in Voice Communications
6.1 Addressing Spoofing and Robocalls
Both STIR/SHAKEN and BCID aim to combat spoofing, which has fueled consumer frustration and regulatory actions. Verified brand displays allow recipients to distinguish legitimate calls from suspicious ones, thereby improving answer rates for genuine businesses.
6.2 CNAM vs. BCID Adoption
- CNAM: Still widely available, but reliant on consumer subscriptions and lacking robust verification. As a result, trust can be low, especially given the high incidence of spoofed caller names.
- BCID: Supported and paid for by businesses, with strong vetting. Over time, BCID’s reliance on cryptographic signatures and brand-specific data is likely to increase consumer confidence in incoming calls.
6.3 Benefits for Businesses
- Higher Answer Rates: Consumers are more inclined to pick up verified calls that display recognizable brand information.
- Improved Reputation: Displaying a consistent, verified identity signals professionalism.
- Reduced Complaints: Clear verification helps differentiate legitimate calls from spam or fraudulent traffic.
7. Challenges and Future Outlook
7.1 Full Carrier Integration
While T-Mobile has deployed the new BCID framework, Verizon and AT&T are still in various stages of rollout. Smaller regional carriers may follow suit as the CTIA standard gains traction.
7.2 Device Compatibility
For BCID to fully function, devices need to support new display fields. Many newer smartphones can handle these updates via carrier settings or OS updates, but older handsets may be incompatible.
7.3 Evolving STIR/SHAKEN
STIR/SHAKEN remains a work in progress, especially for cross-border calls. BCID solutions must adapt to international standards or risk partial functionality in global communications.
7.4 Prospects for Rich Call Data
As carriers become more comfortable with cryptographic verification, the industry may move toward “rich call data,” enabling real-time notifications, interactive call-back options, and other advanced features that further enhance consumer trust.
8. Conclusion
From the early days of CNAM to the advanced Branded Caller ID (BCID) ecosystem emerging today, caller ID technologies are transitioning from basic, largely unverified text fields to robust, cryptographically validated brand displays. While CNAM remains a familiar service—albeit limited by inconsistent adoption and a lack of a vetting process—BCID leverages the STIR/SHAKEN framework to boost consumer confidence in who’s calling.
The unified BCID service championed by the CTIA represents a critical shift: a single, standardized platform for businesses to register and display trusted call information across major carriers. As BCID rolls out more widely, it has the potential to substantially reduce spoofing and rebuild trust in phone-based communications, benefiting both enterprises seeking higher engagement and consumers wary of the spam and fraud that characterize today’s telephony landscape.
References and Further Reading
- CTIA. (2023). Branded Caller ID Specifications and Industry Guidelines. CTIA.org
- Federal Communications Commission (FCC). (2022). STIR/SHAKEN Implementation and Robocall Mitigation. FCC.gov
- TNS. (2023). Enhanced Caller Identity and Call Guardian Solutions. tnsi.com
- First Orion. (2023). Branded Communication Tools and Call Enhancement. firstorion.com
- Hiya. (2023). Call Protection, Caller ID, and Analytics Solutions. hiya.com
- IETF. (2019). Secure Telephone Identity Revisited (STIR). tools.ietf.org